Platform
Features
Firm Management
Growth & Marketing
Firm Operations
Client Operations
Integrations
Practice Area Support
Features
Firm Management
See all features
Document Management
Keep client information secure and easily findable.
Task Management
Track and execute every project your firm undertakes.
Automated Workflows
Automate your manual work to get more of your to-do list done.
Advanced Reporting
Run holistic and insightful reports that support strategic decisions.
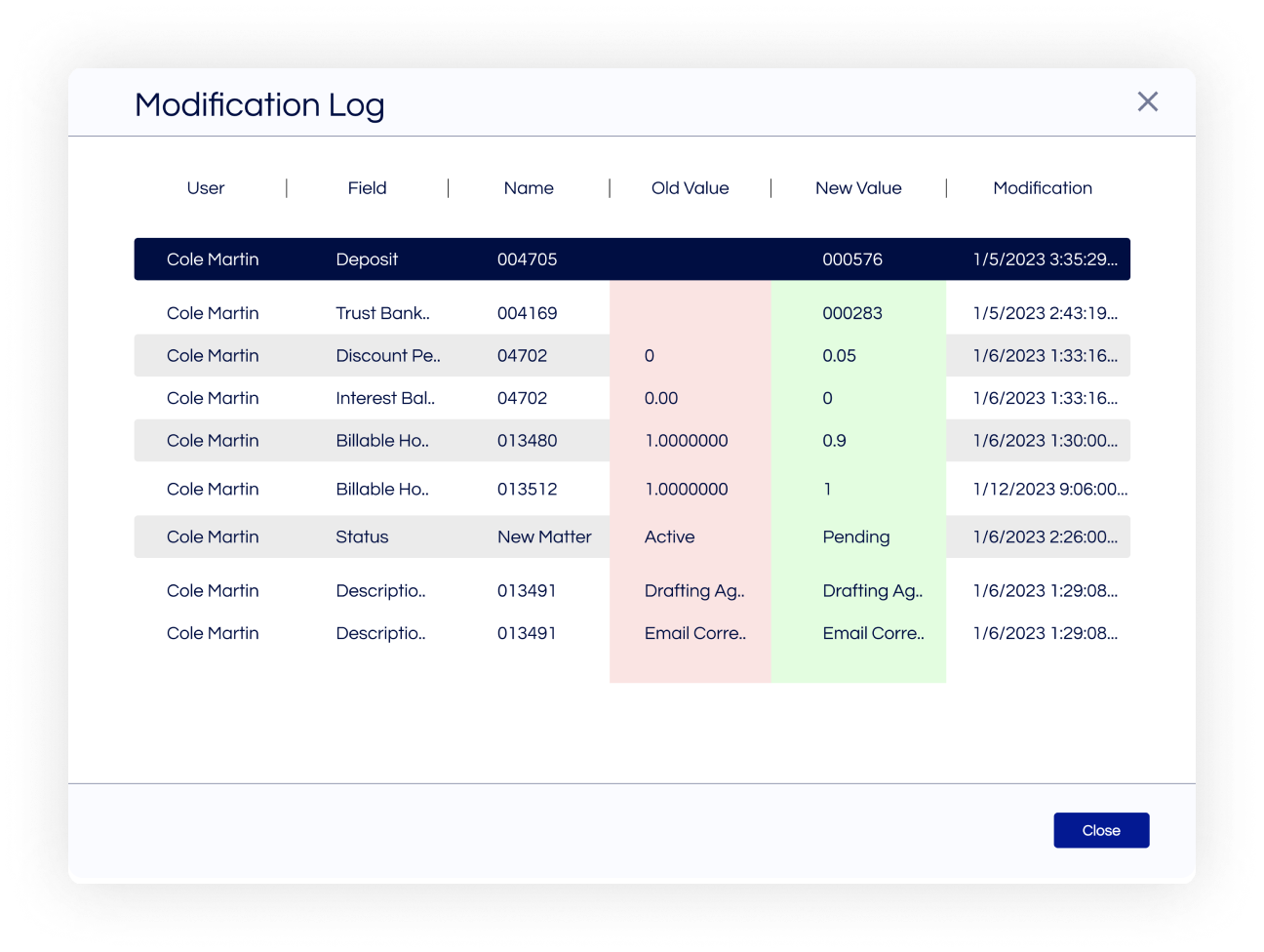
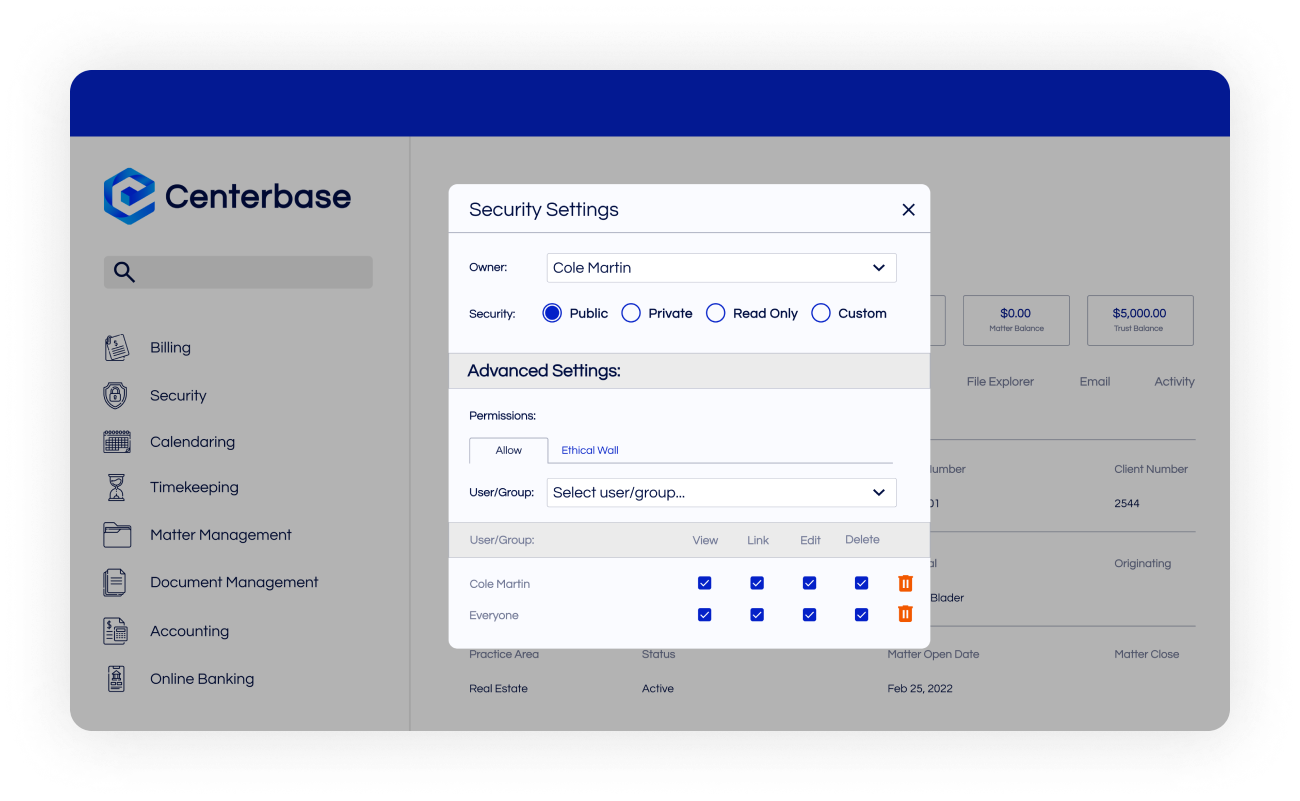
Security
Protect your data from outside and inside threats.
Trust & Retainer Accounting
Feel confident that you’re complying with trust regulations.
Firm Accounting
Easily prove your firm is a fiscally responsible business unit.
Online Banking
Easily reconcile your credit cards with a live online banking feed.
Growth & Marketing
See all features
Production & Origination
Easily credit and compensate originators for their work.
Websites
Increase your firm’s visibility with a high-converting website.
Marketing Services
Execute personalized marketing strategies and track their ROI.
Profitability Reporting
Track and analyze key profit opportunities for your firm.
Firm Operations
See all features
Matter Management
Empower departments to find matter information in one place.
Billing
Bill clients the way they want without burdening your staff.
ePre-bill
Review, edit, and track pre-bills electronically through the approval chain.
Mobile App
Manage your firm and track time from your cell phone.
Calendaring
Filter and compare everyone’s schedule in one calendar.
Client Operations
See all features
Client Portal
Easily update clients before they call you with questions.
Client Intake
Quickly intake new clients before they search for other counsel.
CRM
Keep tabs on every client in one place.
Timekeeping
Empower your attorneys to hit every billable target.
Automated Time Capture
Our automatic timer starts and stops when you do.
Payments
Get client payments within minutes of sending out a bill.
Integrations
LawToolBox
Get your deadlines calculated for you with LawToolBox
Plaid
Make reconciliation easy with Plaid’s live online banking feed.
NetDocuments
Harness the power of NetDocuments right within Centerbase.
QuickBooks
Account for every dollar in Centerbase and QuickBooks Online.
Office365
Use Centerbase within the Microsoft applications you’re used to.
iManage
Use Centerbase with iManage.
Practice Area Software